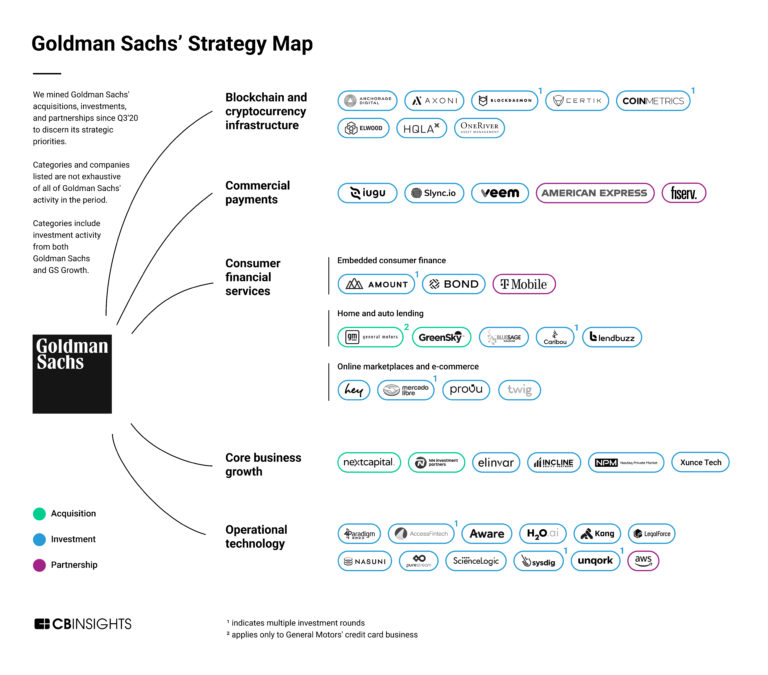
Sysdig
Founded Year
2013Stage
Series G | AliveTotal Raised
$728.2MValuation
$0000Last Raised
$350M | 3 yrs agoMosaic Score The Mosaic Score is an algorithm that measures the overall financial health and market potential of private companies.
-52 points in the past 30 days
About Sysdig
Sysdig provides security for cloud-based systems, containers, and Kubernetes. The company offers a platform that helps detect threats, manage vulnerabilities, control risks across multiple cloud environments, and manage permissions. It primarily serves the cloud computing industry. It facilitates vulnerability management, posture management, cloud monitoring, custom metrics, and more. Its products are Sysdig Platform and Sysdig Monitor. It was formerly known as Draios. It was founded in 2013 and is based in San Francisco, California.
Loading...
Sysdig's Product Videos
ESPs containing Sysdig
The ESP matrix leverages data and analyst insight to identify and rank leading companies in a given technology landscape.
The infrastructure monitoring market focuses on solutions for gaining visibility across IT environments. Infrastructure monitoring typically involves tracking the performance and health of IT components and applications, as well as resolve issues. These solutions enable observability by collecting data that is captured in metrics, logs, and visualizations. Many companies in this market provide AI-…
Sysdig named as Challenger among 13 other companies, including IBM, Datadog, and Elastic.
Sysdig's Products & Differentiators
Sysdig Platform Architecture
Unified visibility across workloads and cloud infrastructure from a single cloud security and monitoring platform. DevOps teams often implement container and Kubernetes security products and Sysdig is unique by providing unified monitoring and security functionality.
Loading...
Research containing Sysdig
Get data-driven expert analysis from the CB Insights Intelligence Unit.
CB Insights Intelligence Analysts have mentioned Sysdig in 6 CB Insights research briefs, most recently on Jul 28, 2023.

Jul 28, 2023
The cloud security market map

Oct 11, 2022
The Transcript from Yardstiq: Klarna vs. Afterpay
Sep 26, 2022 report
Top cloud security companies — and why customers chose themExpert Collections containing Sysdig
Expert Collections are analyst-curated lists that highlight the companies you need to know in the most important technology spaces.
Sysdig is included in 3 Expert Collections, including Unicorns- Billion Dollar Startups.
Unicorns- Billion Dollar Startups
1,249 items
Tech IPO Pipeline
568 items
Cybersecurity
10,248 items
These companies protect organizations from digital threats.
Sysdig Patents
Sysdig has filed 27 patents.
The 3 most popular patent topics include:
- operating system technology
- cloud infrastructure
- computer network security
Application Date | Grant Date | Title | Related Topics | Status |
|---|---|---|---|---|
10/28/2022 | 11/5/2024 | Computer security, Web security exploits, Computer network security, Security compliance, Computer security exploits | Grant |
Application Date | 10/28/2022 |
|---|---|
Grant Date | 11/5/2024 |
Title | |
Related Topics | Computer security, Web security exploits, Computer network security, Security compliance, Computer security exploits |
Status | Grant |
Latest Sysdig News
Nov 4, 2024
We’re looking at cloud credential theft (not good) and a big win for early vulnerability fixes (better) this week, as well as critical Mitsubishi Electric and Rockwell Automation bugs that could affect industrial control environments. Additionally, a SSL certificate weakness in qBittorrent has finally been fixed after 14 years of vulnerability. Also, Microsoft hasn’t yet developed a fix for Windows 11 downgrade attacks, which were first announced this summer at the Black Hat conference. If your business runs Windows operating systems (as most do), check system files for strange activity and any downgrades to older, more vulnerable OS versions. October 26, 2024 Type of vulnerability: Admin code execution privileges leading to operating system downgrades. The problem: This summer, researcher Alon Leviev revealed a downgrade attack vulnerability in Windows, the exploit for which he named Downdate. The Windows update process could be overtaken, and a threat actor could execute undetectable and irreversible downgrades to Windows system components, Leviev said . He demonstrated the downgrade at Black Hat 2024, reverting fully patched Windows machines back to previous vulnerable states. Leviev recently published an update to the summer’s information, showing that Microsoft’s decision not to fix an Administrator privilege makes Windows 11 still vulnerable. Because an admin gaining kernel code execution privileges isn’t considered breaking an official security boundary or vulnerability, Microsoft has opted not to fix it. Microsoft has recently reported it’s actively working on a fix, though it hasn’t provided a deadline or specific details. The fix: Monitor your Windows operating system behavior, including log files, and look for any downgrade procedures. Microsoft has no published fix for the threat yet, since it doesn’t consider it an official vulnerability. I also recommend scanning regularly for vulnerabilities, on an automated basis if possible. Check out our top vulnerability scanning tools for some ideas if your security team needs more consistent monitoring. October 30, 2024 Type of vulnerability: Misconfigured cloud services and exposed Git files. The problem: Sysdig reported a widespread credential theft operation that preys on exposed Git configuration files. Sysdig refers to the global attack as EMERALDWHALE. EMERALDWHALE uses private software tools to abuse misconfigured web services, which helps threat actors steal cloud credentials from cloud services’ source code. Threat actors can also clone private Git repositories. The threat actors then stash any stolen data in a previous victim’s S3 bucket. They’ve stolen over 10,000 cloud credentials thus far, Sysdig reports. Sysdig discovered the threat when it found in its cloud honeypot a strange bucket using a compromised account. “While investigating this bucket, we discovered malicious tools and over a terabyte of data, which included compromised credentials and logging data,” Sysdig said. Through the bucket, Sysdig uncovered an extensive scanning campaign exploiting Git configurations. Two of the major tools that attackers use to exploit the Git config files are MZR V2 and Seyzo-v2, which require a list of targets like IP addresses or previously scanned domains. The tools are found on underground marketplaces. The fix: Use encryption for all your Git configuration; avoid committing sensitive data, including credentials; and set strict access requirements for your repositories. October 31, 2024 Type of vulnerability: Missing authentication for critical function and unsafe reflection. The problem: CVE-2023-6943 , a Mitsubishi vulnerability that was publicized in January, has been updated and highlighted through the CISA. The vulnerability has a critical score of 9.8 and affects components like EZSocket, MELSOFT Navigator, and MT Works2. On Halloween, the CISA released a set of advisories for three of the Mitsubishi vulnerabilities and the Rockwell Automation bug listed below. The advisories are considered to be a broad industrial control warning. These flaws could particularly affect smart devices in manufacturing and supply chain environments. “Successful exploitation of these vulnerabilities could allow an attacker to disclose, tamper with, destroy or delete information in the products, or cause a denial-of-service (DoS) condition on the products,” the CISA said regarding CVE-2023-6943, the critical Mitsubishi vulnerability. A remote unauthenticated threat actor could execute code using paths to a malicious library when it’s connected to any of the Mitsubishi products listed above. The CISA listed the affected versions of each product: EZSocket: Versions 3.0 and later GT Designer3 Version1(GOT1000): All versions GT Designer3 Version1(GOT2000): All versions GX Works2: Versions 1.11M and later GX Works3: Versions 1.106L and prior MELSOFT Navigator: Versions 1.04E and later MT Works2: All versions MX OPC Server DA/UA (Software packaged with MC Works64): All versions The fix: For GX Works3, Mitsubishi Electric advises customers to upgrade to version 1.110Q or later . Rockwell Automation Bug Also Gets CISA Warning Type of vulnerability: Missing authentication for critical function and out-of-bounds read. The problem: A critical Rockwell Automation bug allows an attacker with network access to send specially crafted messages to the Rockwell device. This could potentially lead to database manipulation. The vulnerability is tracked as CVE-2024-10386 and specifically affects Rockwell FactoryTalk ThinManager. The CISA released a notice for the vulnerability and warns that potential messages sent to the Rockwell device could also lead to a denial-of-service (DoS) attack. The vulnerability affects the following software versions: ThinManager: Versions 11.2.0 to 11.2.9 ThinManager: Versions 12.0.0 to 12.0.7 ThinManager: Versions 12.1.0 to 12.1.8 ThinManager: Versions 13.0.0 to 13.0.5 ThinManager: Versions 13.1.0 to 13.1.3 ThinManager: Versions 13.2.0 to 13.2.2 ThinManager: Version 14.0.0 The fix: Rockwell has provided fixes for ThinManager ; download the most recent version available for your environment. November 1, 2024 Type of vulnerability: Insufficient SSL certificate validation, potentially leading to remote code execution. The problem: qBittorrent has a recently discovered and patched vulnerability that went unidentified for 14 years. Versions 3.2.1 through 5.0.0 of the software, a torrent client that helps with sequential downloading, are susceptible to a severe security issue. If exploited, the vulnerability allows threat actors to run remote code on computer systems with an affected version installed. The flaw existed in qBittorrent’s DownloadManager class. It didn’t deal with SSL certificate validation errors, which leaves website connections vulnerable. The fix: Version 5.0.1 of qBittorrent fixes the issue, and all vulnerable versions should be upgraded. Google’s Big Sleep Framework Identifies Vulnerability Early Type of vulnerability: Stack buffer overflow. The problem: Google Project Zero recently announced that Big Sleep, a vulnerability research project supported by large language models, discovered its first vulnerability. The flaw lies within SQLite, a database engine, and is a stack buffer overflow vulnerability that Google reported to SQLite’s developers, who fixed it that day. Because the devs fixed the issue before it was announced, it didn’t impact SQLite users. This is an exciting discovery for Google Project Zero because it heralds the future of identifying vulnerabilities before they’re even publicly available to exploit within software. This significantly reduces threat actors’ opportunities to attack. The fix: Upgrade SQLite to the most recent version. Read next:
Sysdig Frequently Asked Questions (FAQ)
When was Sysdig founded?
Sysdig was founded in 2013.
Where is Sysdig's headquarters?
Sysdig's headquarters is located at 135 Main Street, San Francisco.
What is Sysdig's latest funding round?
Sysdig's latest funding round is Series G.
How much did Sysdig raise?
Sysdig raised a total of $728.2M.
Who are the investors of Sysdig?
Investors of Sysdig include Accel, Bain Capital Ventures, Insight Partners, Glynn Capital Management, Goldman Sachs and 12 more.
Who are Sysdig's competitors?
Competitors of Sysdig include Grafana Labs, Wiz, Aqua Security, Upwind, AccuKnox and 7 more.
What products does Sysdig offer?
Sysdig's products include Sysdig Platform Architecture and 2 more.
Who are Sysdig's customers?
Customers of Sysdig include Beekeeper, WorldPay from FIS and SAP Concur.
Loading...
Compare Sysdig to Competitors

Wiz provides cloud security software within the cybersecurity industry. Its main offerings include a unified cloud security platform that enables security, development, and operations teams to collaborate and secure cloud environments effectively. Wiz's platform offers solutions for continuous security posture management (CSPM), container and Kubernetes security, cloud workload protection (CWPP), identity and access management (CIEM), and data security posture management (DSPM), among others. It was founded in 2020 and is based in New York, New York.

Aqua Security specializes in cloud-native security. The company offers a comprehensive cloud-native application protection platform that provides prevention, detection, and response automation across the entire application lifecycle, securing the build, cloud infrastructure, and running workloads. It primarily serves sectors such as finance and the federal government. Aqua Security was formerly known as Scalock. It was founded in 2015 and is based in Burlington, Massachusetts.

Uptycs is a cloud security company that specializes in protecting hybrid cloud environments and providing visibility from development to runtime. The company offers a suite of security solutions including workload protection, compliance automation, threat detection and response, and security for containers and Kubernetes. Uptycs serves enterprises by optimizing security operations, ensuring compliance, and accelerating remediation across cloud workloads, containers, Kubernetes, and software pipelines from a unified security console. It was founded in 2016 and is based in Waltham, Massachusetts.

Orca Security focuses on cloud security. It offers a cloud security platform that provides services such as identifying and remediating misconfigurations across clouds, protecting virtual machines, containers, and serverless functions, and monitoring and responding to threats across the cloud attack surface. The company primarily sells to sectors such as financial services, technology, government, retail, healthcare, and media & entertainment. It was founded in 2018 and is based in Portland, Oregon.

Upwind operates as a company focused on cloud security in the technology sector. It offers services such as threat detection, vulnerability management, and cloud security posture management, all aimed at securing hosts, containers, virtual machines, and serverless functions. The company primarily serves the cloud computing industry. It was founded in 2022 and is based in San Francisco, California.

Fairwinds is a company that focuses on providing Kubernetes enablement solutions in the cloud-native infrastructure sector. The company offers a range of services including managed services, advisory services, and software solutions aimed at improving security and reducing costs for cloud-native infrastructure. Their primary market is organizations looking to adopt or optimize their use of cloud-native infrastructure. Fairwinds was formerly known as ReactiveOps. It was founded in 2015 and is based in Boston, Massachusetts. Fairwinds operates as a subsidiary of Bob Brennan, Robert Ketterson, and William Ledingham.
Loading...