Druva
Founded Year
2008Stage
Secondary Market | AliveTotal Raised
$475MRevenue
$0000Mosaic Score The Mosaic Score is an algorithm that measures the overall financial health and market potential of private companies.
-55 points in the past 30 days
About Druva
Druva provides data security solutions and specializes in cloud-based backup and protection services for various business sectors. The company offers a SaaS platform that secures and recovers data across enterprise, cloud, and SaaS environments, focusing on data protection, cyber response and recovery, and data governance. Druva's services are designed for organizations aiming to meet data protection regulations. It was founded in 2008 and is based in Santa Clara, California.
Loading...
ESPs containing Druva
The ESP matrix leverages data and analyst insight to identify and rank leading companies in a given technology landscape.
The data governance & privacy market helps organizations manage and protect data throughout its lifecycle to meet regulatory requirements, such as those associated with GDPR and HIPAA. With the explosion of digital transformation and cloud adoption, this market has become increasingly important for organizations looking to scale securely and automate their operations. The market offers intelligenc…
Druva named as Challenger among 15 other companies, including Microsoft, Talend, and BigID.
Loading...
Research containing Druva
Get data-driven expert analysis from the CB Insights Intelligence Unit.
CB Insights Intelligence Analysts have mentioned Druva in 7 CB Insights research briefs, most recently on Mar 14, 2024.

Mar 14, 2024
The retail banking fraud & compliance market map
Sep 6, 2023
The data security market map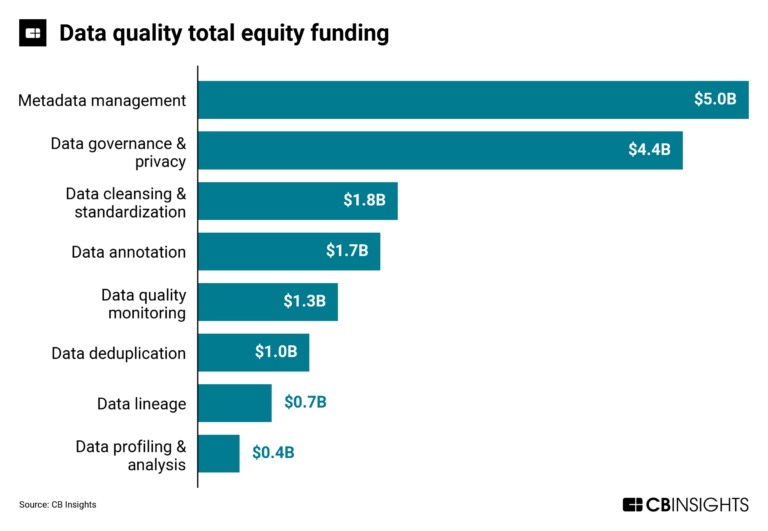
Jul 31, 2023
The data quality market map
Jul 28, 2023
The cloud security market map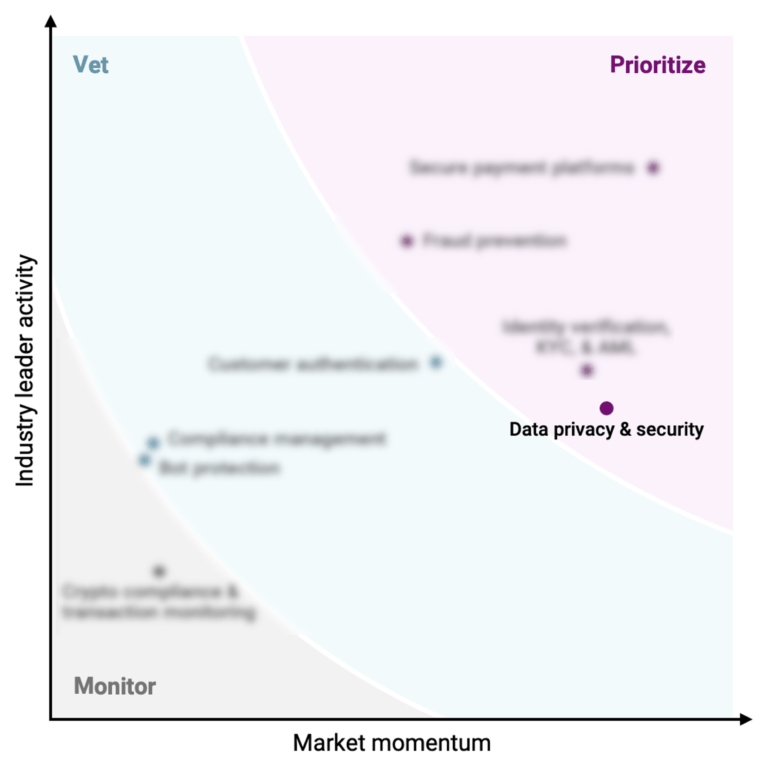
May 5, 2022 report
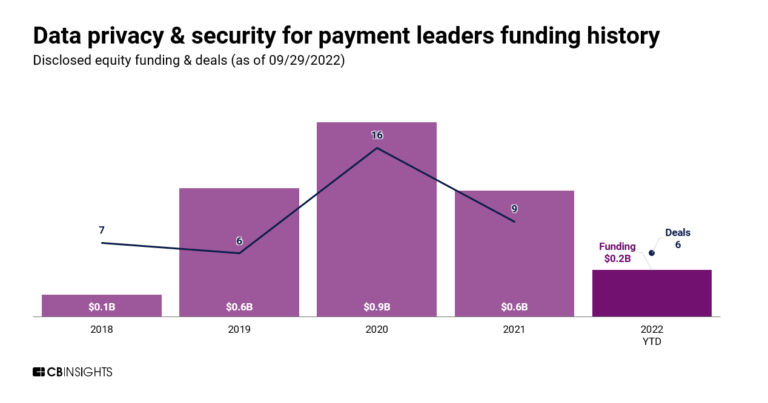
Why payments leaders are prioritizing data privacy & securityExpert Collections containing Druva
Expert Collections are analyst-curated lists that highlight the companies you need to know in the most important technology spaces.
Druva is included in 6 Expert Collections, including Unicorns- Billion Dollar Startups.
Unicorns- Billion Dollar Startups
1,249 items
Regtech
1,721 items
Technology that addresses regulatory challenges and facilitates the delivery of compliance requirements. Regulatory technology helps companies and regulators address challenges ranging from compliance (e.g. AML/KYC) automation and improved risk management.
Tech IPO Pipeline
282 items
Track and capture company information and workflow.
Work From Home Startups
91 items
Track startups and capture company information and workflow.
Cybersecurity
10,248 items
These companies protect organizations from digital threats.
Defense Tech
1,273 items
Defense tech is a broad field that encompasses everything from weapons systems and equipment to geospatial intelligence and robotics. Company categorization is not mutually exclusive.
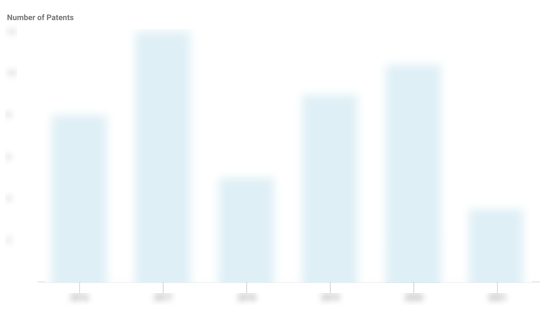
Druva Patents
Druva has filed 65 patents.
The 3 most popular patent topics include:
- cloud storage
- data management
- backup
Application Date | Grant Date | Title | Related Topics | Status |
|---|---|---|---|---|
5/11/2022 | 10/15/2024 | Backup, Disaster recovery, Cryptography, Cloud storage, Data security | Grant |
Application Date | 5/11/2022 |
|---|---|
Grant Date | 10/15/2024 |
Title | |
Related Topics | Backup, Disaster recovery, Cryptography, Cloud storage, Data security |
Status | Grant |
Latest Druva News
Oct 1, 2024
Infosec products of the month: September 2024 Here’s a look at the most interesting products from the past month, featuring releases from: Absolute, anecdotes, ArmorCode, Binarly, Bitdefender, Druva, F5 Networks, Gcore, Guardsquare, Huntress, Ketch, LOKKER, Malwarebytes, NETGEAR, Nudge Security, Prompt Security, Rapid7, Revenera, Skyhigh Security, Strivacity, Tenable, Trellix, Vanta, Veritas Technologies, and Wing Security. Bitdefender Security for Creators protects YouTube content creators and influencers from hackers Bitdefender Security for Creators safeguards content channels and social media accounts from takeovers and supports Windows, Mac, Android, and iOS. Set-up takes a few moments and connects to both content channel and owner. Once activated, Bitdefender continuously monitors for anomalous behaviors on channels and scans owner devices (computers, tablets, mobile) for phishing emails, malicious URLs, files, and malware sending alerts in real-time. Prompt Security helps organizations monitor data shared with Microsoft 365 Copilot Prompt Security launched a security and governance solution for Copilot for Microsoft 365 . The solution addresses use cases such as internal and external data privacy, content moderation, observability, user activity analytics, and facilitating auditing and compliance with multiple regulatory standards. Binarly Transparency Platform 2.5 identifies critical vulnerabilities before they can be exploited The new Binarly Transparency Platform 2.5 empowers organizations with the tools to proactively mitigate firmware and software security issues. By integrating Reachability Analysis and other advanced features, the platform enables enterprise defenders to avoid alert fatigue while identifying and addressing critical vulnerabilities before they can be exploited by malicious actors Skyhigh AI mitigates risks associated with AI applications Skyhigh AI significantly reduces the risks associated with enterprise usage of AI applications through increased visibility, improved protection, and ensured compliance. Skyhigh AI uses AI and ML within its SSE platform to improve security operations by increasing efficiency and productivity while reducing complexity, risk and costs. Vanta empowers GRC teams to make their security and compliance automated Vanta’s new Report Center , enhancements to VRM and milestone achievements for pre-built integrations and frameworks give GRC and security teams always-on visibility with actionable insights so they can establish and promote trust internally and externally. Revenera OSS Inspector enables developers to assess open source software risks The Revenera OSS Inspector plugin enables developers using IntelliJ IDEA, an integrated development environment (IDE), to examine, within the IDE itself, the licenses and security vulnerabilities associated with the OSS components used in the application code. Without leaving the IDE, developers can immediately assess security risks to determine whether they require further review and remediation. Tenable AI Aware provides exposure insight into AI applications, libraries and plugins Tenable AI Aware leverages agents, passive network monitoring, dynamic application security testing and distributed scan engines to detect approved and unapproved AI software, libraries and browser plugins, along with associated vulnerabilities, thereby mitigating risks of exploitation, data leakage and unauthorized resource consumption. SaaS Pulse tool from Wing Security enhances SaaS security posture Wing Security has released SaaS Pulse , a free tool for SaaS security management, offering organizations actionable insights and continuous oversight into their SaaS security posture. This tool continuously monitors threats from issues like critical misconfigurations, offboarding errors, user access risks, and more. LOKKER’s consent management solution blocks all unauthorized data collection on websites LOKKER released a new consent management solution available in its Privacy Edge Platform. LOKKER’s solution can work as a standalone product or alongside a company’s existing CMP to proactively detect and block pixels, tags and trackers and the cookies they set that can serve in a “Reject All” state. Huntress launches Managed SIEM, eliminating the complexity of traditional SIEMs Huntress’ SIEM will combine proprietary Smart Filtering of security data, streamlined log storage, hands-off management, and continuous monitoring by Huntress’ elite team of experts to stay ahead of threats—with a transparent, predictable cost model. Trellix strengthens email security with DLP capabilities Trellix Email Security Cloud stops advanced threats through multi-layered detection powered by Trellix Wise AI. By integrating DLP capabilities into email security, organizations can now address both inbound malicious threats and outbound loss of sensitive information in one solution. Dru Investigate simplifies cyber investigations and helps users uncover data threats Dru Investigate is designed to empower users to investigate potential data risks with natural language queries so they can quickly understand their data – even guiding them when they do not know what to look for. When used, this AI-enabled capability significantly streamlines and simplifies investigative processes and drives faster outcomes, whether remediating and recovering from a threat or upholding rigorous data compliance. Ketch helps media brands enable privacy-safe data activation Ketch Data Permissioning for Media Companies ensures media companies can activate data with confidence, from dynamic preference collection to real time data stack enforcement and visibility. With Ketch, digital media brands can optimize consent rates, increase identity resolution, and enhance audience quality. Veritas unveils AI-driven features to simplify cyber recovery Veritas Technologies unveiled new AI-driven capabilities to further expand the strength and functionality of the Veritas cyber resilience portfolio. The new innovations, including AI-powered automation and user interface enhancements, provide data protection specialists and IT generalists with intelligent, easy-to-use solutions that remove the uncertainty from cyber recovery. F5 NGINX One improves app delivery and security functions NGINX One improves app security and delivery for development, operations, and platform teams by making it easier to own, optimize, and govern NGINX components in any context. With the NGINX One Console, teams can broadly and easily enforce security policies across the application ecosystem, receive and implement configuration guidance, and automate version and patch updates—all helping to ensure compliance. Rapid7 launches Vector Command for continuous red teaming and security gap identification Vector Command delivers a continuous discovery, assessment, and validation service that goes beyond vulnerabilities to confirm that the overall state of an organization’s IT security posture and controls are sufficient in thwarting would-be adversaries. Strivacity AI Assist optimizes digital identity management Strivacity released Strivacity AI Assist , a new “smart assistant” powered by GenAI that makes it easier to manage and secure digital identities across business-to-business (B2B) and business-to-consumer (B2C) use cases. Anecdotes Trust Center simplifies compliance and security documentation sharing Anecdotes Trust Center continuously pulls data directly from a company’s Anecdotes Compliance OS, ensuring all documentation is up-to-date and accurate and reducing the risk of errors that can occur when multiple teams are involved in the documentation process. Gcore WAAP protects websites, web applications, and APIs Gcore WAAP continuously monitors and analyses web application and API traffic at the edge, mitigating threats before they reach protected resources. It automatically scales to maintain consistent protection without compromising web performance. With AI-driven threat detection, behavioural analysis, and machine learning, WAAP uses insights from Gcore’s edge platform to identify patterns of malicious activity. ArmorCode unveils two modules to help reduce software-based risks ArmorCode announced the expansion of its platform with the launch of two new modules for Penetration Testing Management and Exceptions Management. Alongside AI-powered Correlation and Remediation, these modules further advance ArmorCode’s platform capabilities to reduce the time, effort, and cost of addressing the riskiest vulnerabilities from any source through any remediation, mitigation, or exception workflow. Guardsquare strenghtens mobile application security for developers Available for both iOS and Android apps, Guardsquare’s latest innovation allows all developers – regardless of their security expertise – to implement the highest level of protection for their mobile apps, preventing reverse engineering and tampering. Absolute AI Threat Insights monitors, detects, and prioritizes suspicious activity With the AI Threat Insights module activated, customers using Absolute to continuously monitor all network traffic across PC fleets can detect and act against zero-day threats, ransomware, other malware, and suspicious user, device and application behaviors. Nudge Security introduces automated SaaS spend discovery capabilities Instead of relying on data from accounting systems, Nudge Security’s discovery method uses machine learning to scan Google Workspace or Microsoft 365 environments to uncover SaaS identities, activities, and risks. Now, the product automatically finds SaaS invoices and receipts in mailboxes to unearth SaaS spend data such as amount, billing frequency, renewal dates, billing owner, and subscription information. Malwarebytes Personal Data Remover protects user privacy Malwarebytes Personal Data Remover scans a network of data broker databases and people search sites, assisting users in removing their personal details, and offering ongoing monitoring to maintain their online privacy, automating up to 318 hours of work a consumer would have to undertake themselves. NETGEAR announces three WIFI 7 routers to secure connectivity for homes of any size NETGEAR expanded its Nighthawk WiFi 7 standalone router line to include the new RS600, RS500, and RS200. Powered by encryption protocols and advanced threat detection mechanisms, NETGEAR routers stand as the first line of defense against evolving cyber threats by including security features such as automatic firmware updates, VPN support, cutting-edge WPA3 security, access control, and guest WiFi network options. More about
Druva Frequently Asked Questions (FAQ)
When was Druva founded?
Druva was founded in 2008.
Where is Druva's headquarters?
Druva's headquarters is located at 2051 Mission College Boulevard, Santa Clara.
What is Druva's latest funding round?
Druva's latest funding round is Secondary Market.
How much did Druva raise?
Druva raised a total of $475M.
Who are the investors of Druva?
Investors of Druva include Fabrica Ventures, Neuberger Berman, Atreides Management, Viking Global Investors, Caisse de depot et placement du Quebec and 14 more.
Who are Druva's competitors?
Competitors of Druva include Clumio, Own Company, Code42, CTERA, Rubrik and 7 more.
Loading...
Compare Druva to Competitors

Cohesity provides data security and data management solutions. The company offers a platform to secure, manage, and extract value from data, providing services such as data protection, threat detection, data mobility, and data insights. It serves sectors such as financial services, healthcare, and government. The company was founded in 2013 and is based in San Jose, California.

Nasuni focuses on file data services, operating within the hybrid cloud storage industry. The company offers a cloud-native suite of services that replace traditional file infrastructure, providing effortless scalability, and built-in security. Its services are primarily utilized by sectors such as manufacturing, construction, technology, oil and gas, financial services, and the public sector. It was founded in 2009 and is based in Boston, Massachusetts.

Veritas provides enterprise data management, focusing on multi-cloud data management solutions. The company offers a suite of services including data protection, application resiliency, and data compliance and governance, aimed at ensuring the protection, recoverability, and compliance of enterprise data. It was founded in 1983 and is based in Santa Clara, California.

HYCU specializes in data protection as a service within the information technology sector. The company offers multi-cloud backup solutions, disaster recovery services, and data migration and mobility, focusing on ensuring data recoverability and application-consistent backup for businesses. HYCU's solutions cater to various sectors, including the public sector and federal industries. It was founded in 2018 and is based in Boston, Massachusetts.

Rewind specializes in cloud data backups and SaaS data protection across various industries. The company offers automated backup solutions and data recovery services to safeguard businesses' critical data. Rewind's services enable clients to recover from data loss quickly and maintain compliance with data regulations. It was founded in 2015 and is based in Ottawa, Ontario.

Assured Data Protection specializes in data backup, business continuity, disaster recovery, and threat detection within the managed services sector. The company offers managed backup solutions, disaster recovery services, and cloud backup for various platforms, ensuring continuous data protection and operational resilience. Assured Data Protection primarily serves customers, MSPs, and resellers across the globe, delivering scalable solutions to enhance data management efficiency. It was founded in 2016 and is based in Leeds, United Kingdom.
Loading...